Phreaky
Phreaky is a medium web challenge that was part of the HTB 2024 CyberApocalypse CTF.
Challenge Hint: In the shadowed realm where the Phreaks hold sway, A mole lurks within, leading them astray. Sending keys to the Talents, so sly and so slick, A network packet capture must reveal the trick. Through data and bytes, the sleuth seeks the sign, Decrypting messages, crossing the line. The traitor unveiled, with nowhere to hide, Betrayal confirmed, they’d no longer abide.
Video Walkthrough
Enumeration
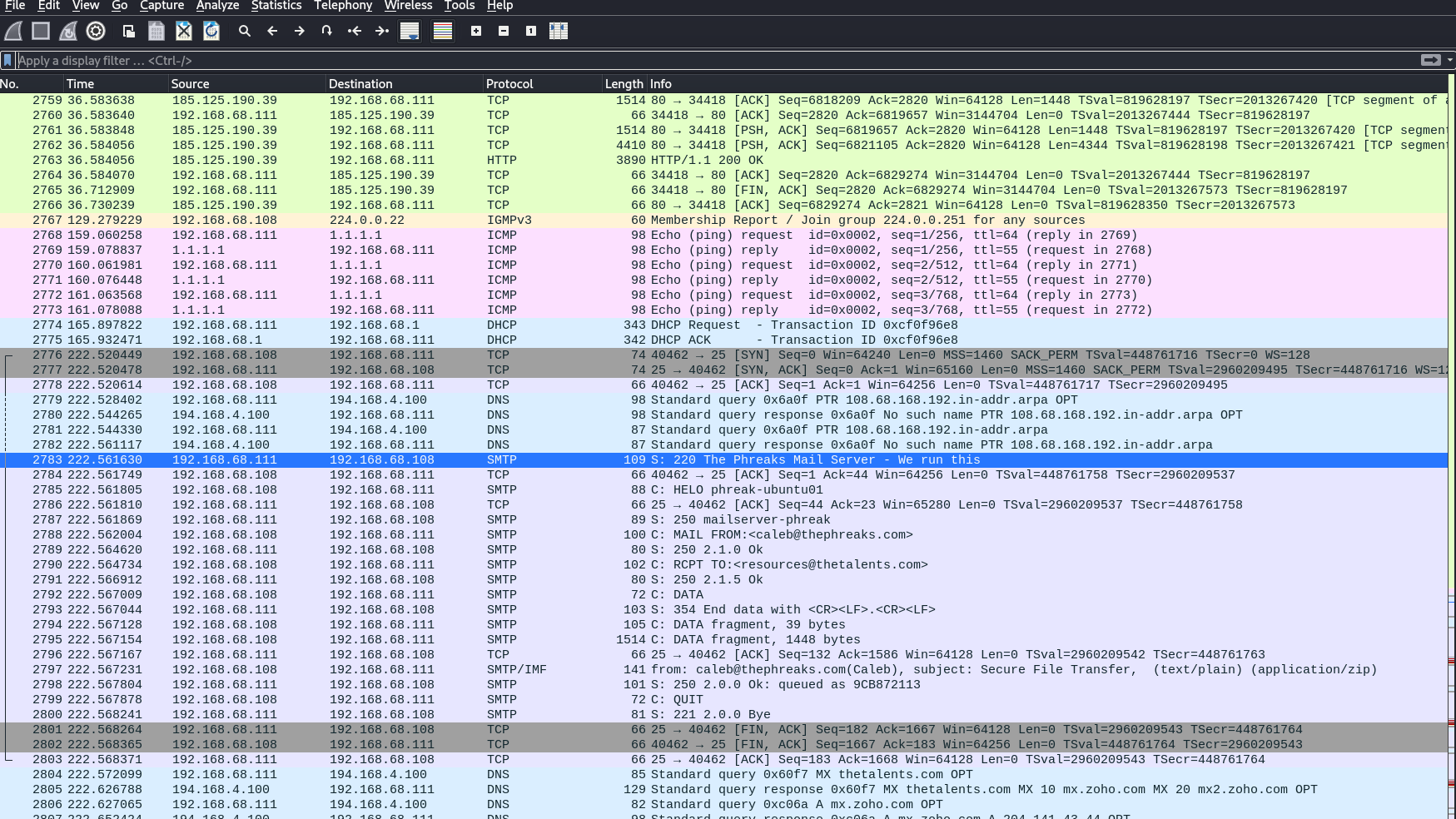
For this challenge, we are just given a pcap (packet capture) file to download, along with the hint above. Let’s open it up with wireshark and see what we can find.
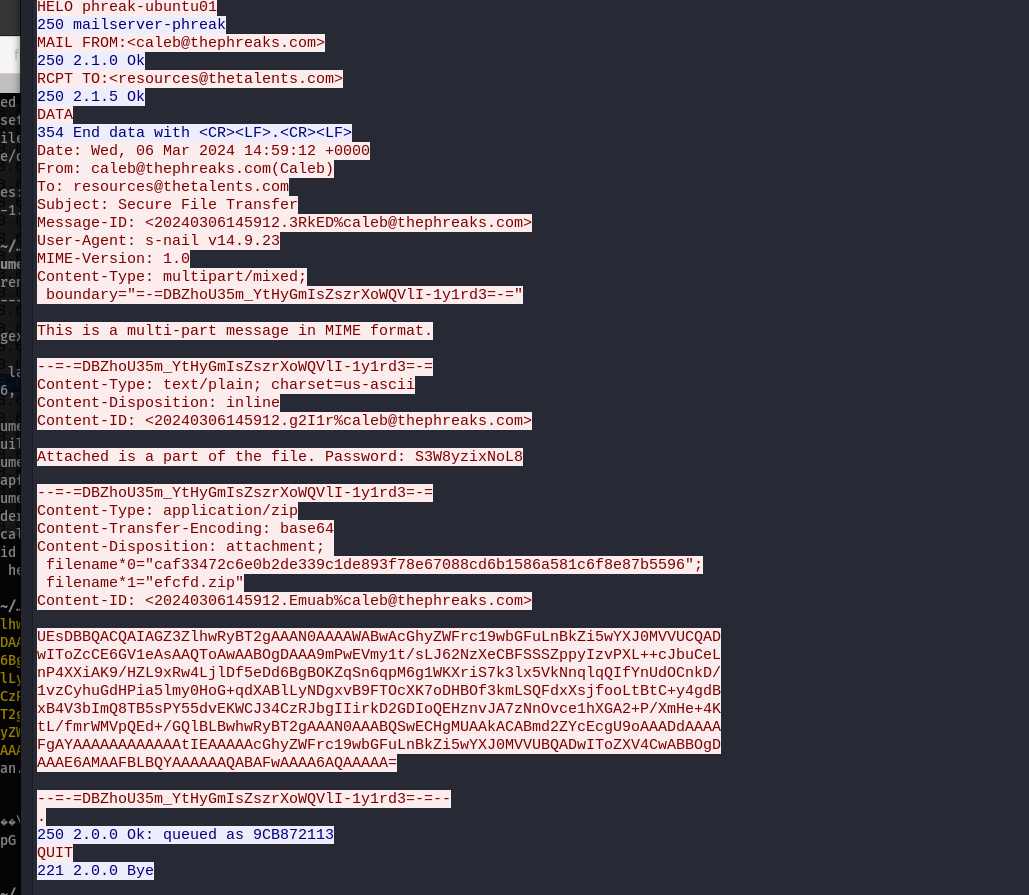
There is a lot to go through in this pcap, but after searching through it for a while, I noticed that there were some emails being sent that appear to have password protected .zip files attached. It also tells us that it is a multi-part message.
NetworkMiner
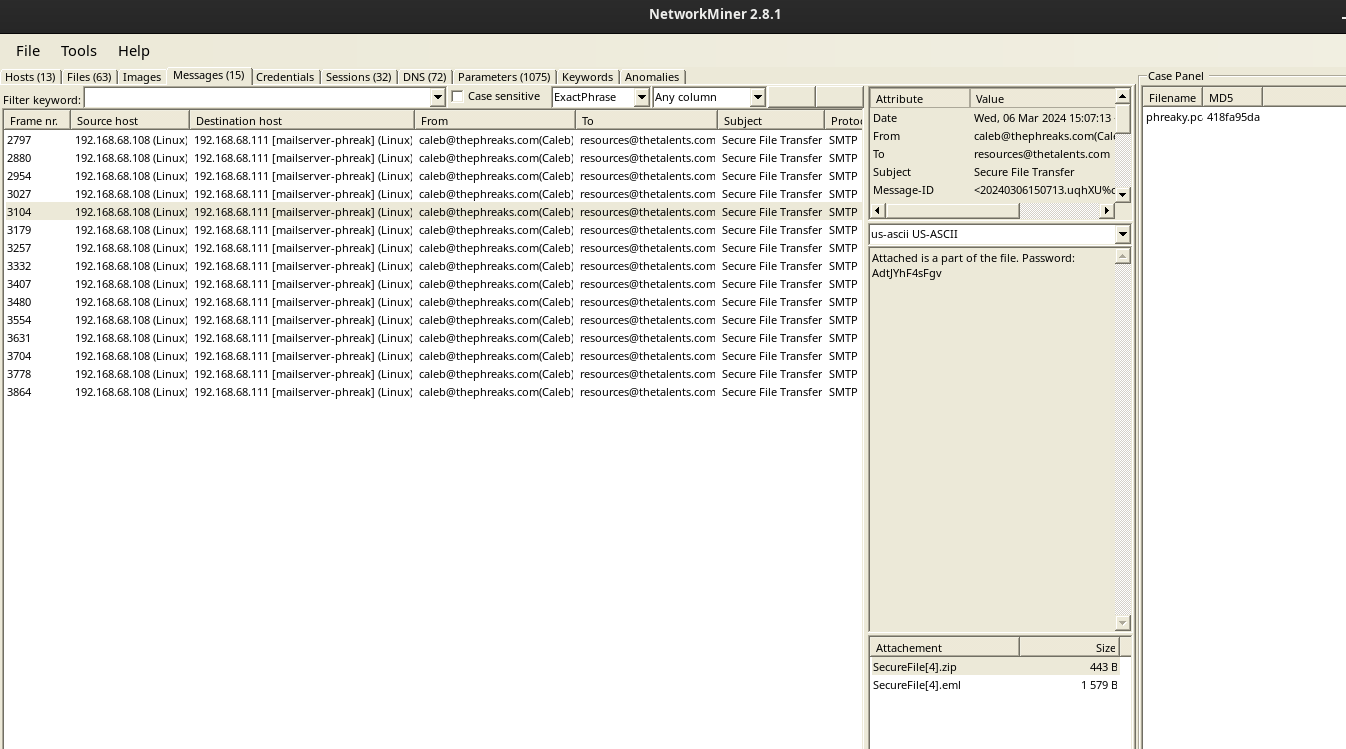
To make it easier to exctract these files, I’m going to switch over to another tool called NetworkMiner. If you open the pcap file and go to the “Messages” tab, you can see a list of all of the emails, the passwords in the messages, and the attachments.
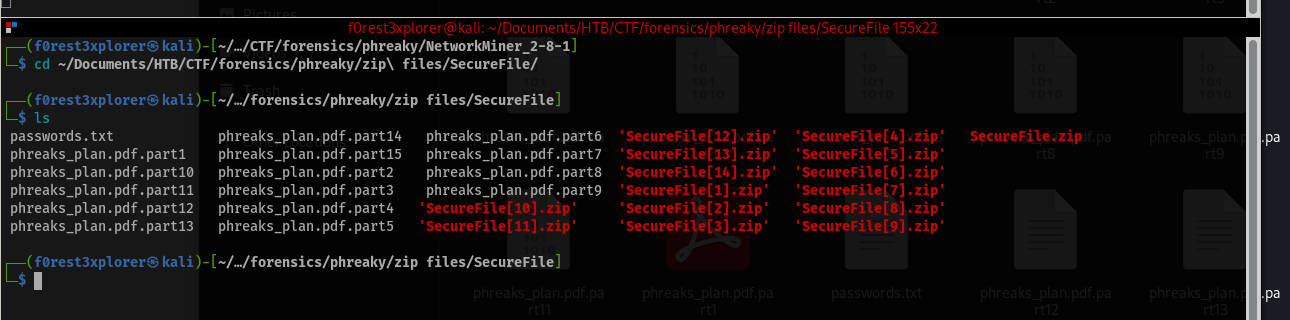
If you right click on one of the attachemnts, you can click on “Show Folder” and it will bring up a finder window with all 15 .zip files along with the corresponding .eml files. If we try and open one of the .zip files, it prompts us for a password. My next step was to make a wordlist of the passwords contained in the emails to make my life a little easier and then unzip all 15 files.
Using cat to combile the files
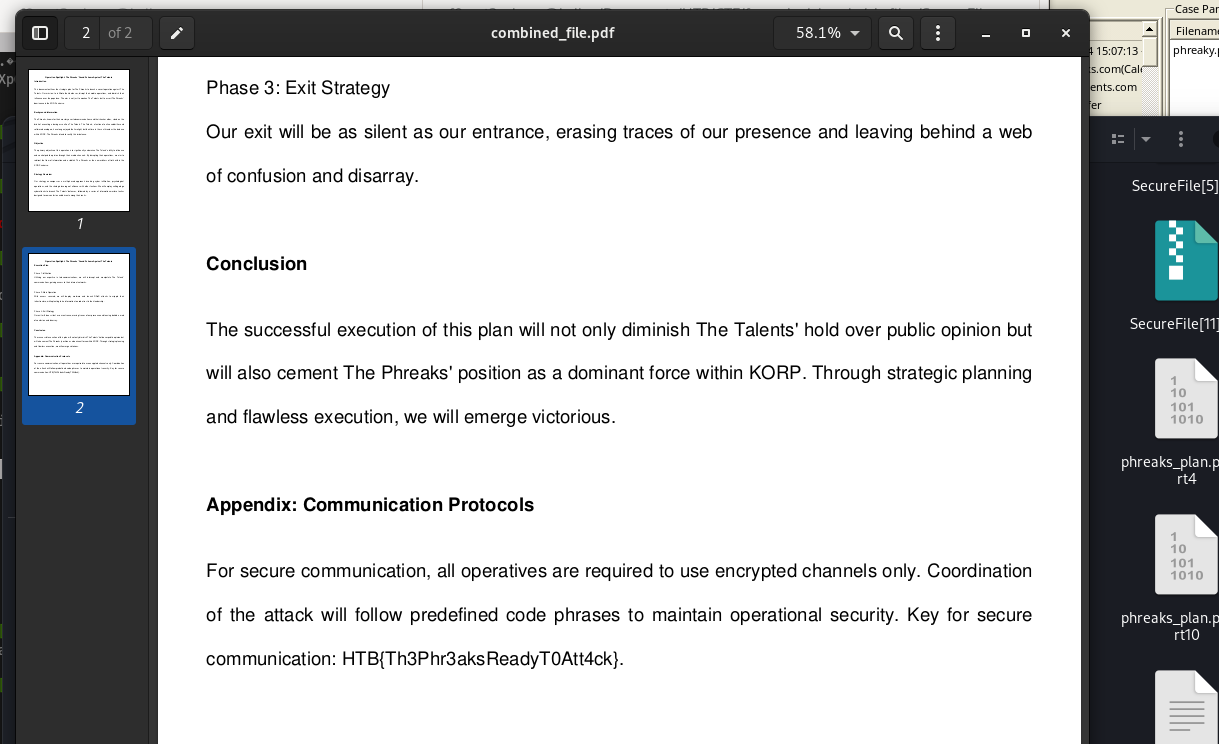
None of the files will open as they are right now. Since we know it was a multipart message, and each PDF filename contains a “part[1-15]”, we need to combine the files back together into one file.
To do this we will use the cat command to concatenate all of the files:
1
2
┌──(f0rest3xplorer㉿kali)-[~/…/forensics/phreaky/zip files/SecureFile]
└─$ cat phreaks_plan.pdf.part* > combined_file.pdf
Flag!
Now we can open combined_file.pdf and we see our flag at the bottom of page 2!